 The news is filled with stories of alarming cybersecurity breaches, networks being hacked, and malware running amok. However, there’s another, less obvious yet equally insidious cybersecurity risk lurking inside just about every organization: inadequate segregation of duties (SOD).
The news is filled with stories of alarming cybersecurity breaches, networks being hacked, and malware running amok. However, there’s another, less obvious yet equally insidious cybersecurity risk lurking inside just about every organization: inadequate segregation of duties (SOD).
In enterprise resource planning (ERP)-dependent business environments, SOD is a highly complex organization control that’s critical to many other business controls. Understanding that SOD analysis is a business control and that the business—not the IT department—is responsible for ensuring it’s performed at regular intervals adds a valuable layer of risk management.
Why SOD Matters
SOD is meant to help ensure responsibilities for essential or consequential business functions are dispersed between more than one person or department. Without this separation, risks ranging from asset theft to fraudulent financial statement manipulation become significantly more difficult to manage.
Why It’s Often Neglected
System-enforced access controls that are part of SOD controls generally rely on IT systems to operate and are often erroneously considered IT controls because of it. SOD is a business control that leverages IT systems to be enforced, which means the IT department simply manages the technological aspects of that control.
The power of SOD isn’t always adequately appreciated because of this, and it’s often viewed as having the same priority as other transaction-level internal controls. This lower level of security prioritization usually results in poorly designed system access rights and other inefficient or ineffective SOD security processes.
Consequences
As technology becomes more pervasive, the risk of fraud increases. While cloud-based ERP systems can increase business efficiency and flexibility, for example, they require stronger access controls due to their heightened security risk. Because modern ERP systems often rely on role-based security and have many different methods to process transactions, potential conflicts often number in the tens of thousands.
Common Pitfalls
To understand the extent of any organization’s SOD status, it’s imperative to use a systematic and rational evaluation approach. Without performing an analysis, SOD issues are only apparent after an incident occurs. If there’s more than one application in the environment—the case for almost every business—it’s likely that inter-application risks haven’t been considered.
Common causes of SOD conflicts within an organization include the following:
- Assuming that SOD was fully considered as part of the ERP system implementation
- Lacking clear accountability for and oversight of system access rights
- Setting up roles with little consideration of formal SOD
- Failing to remove old access rights after organizational change and personnel moves
- Lacking technical and policy coordination
Next Steps
The assessment of an organization’s SOD can be difficult, complex, and time consuming, but there are many off-the-shelf systems available to help facilitate the process. Depending on the application, these tools can often be built into preexisting systems offered as a third-party module, a stand-alone application, or as a cloud-based service. Oracle Enterprise GRC Manager, SAP GRC, Fastpath, ERP Maestro, and other similar tools streamline the analysis and administration of an SOD review significantly.
Business Process Segregation of Duties
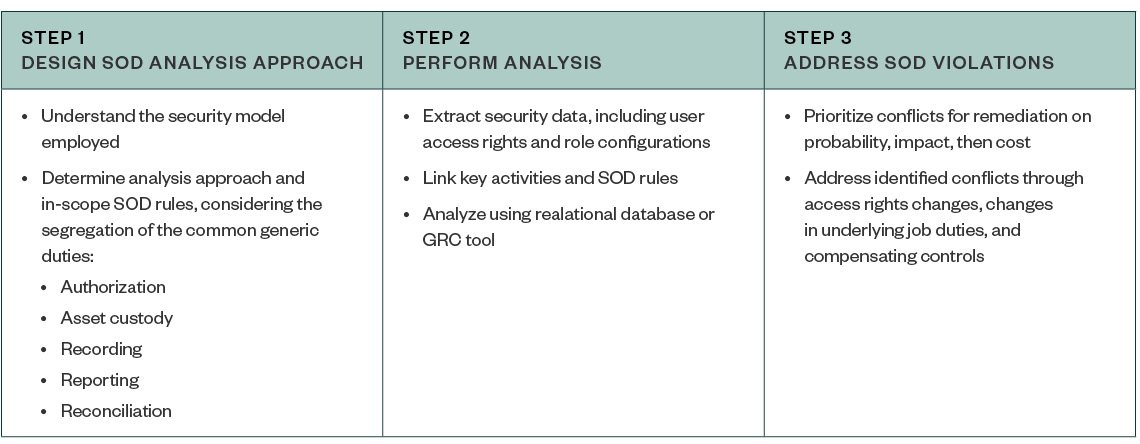
Analyzing SOD Controls
Defining what activities are fundamental to the business and should be appropriately segregated is a critical step in analyzing SOD. This helps determine how conflicts should be identified and addressed.
When analyzing controls for these fundamental activities, it’s prudent for organizations to:
- Consider the appropriate segregation of duties within their IT processes
- Understand how security is administered within the system
- Remember that customized changes to a purchased application might affect what and how access rights are analyzed
Each SOD conflict has its own risk profile and prioritizing each type of conflict is critical. There’s no precise number of SOD rules that an organization should establish. Some organizations have a higher degree of inherent risk or a more complex environment that may warrant more rules; others don’t. Regardless of the scope of SOD conflicts within an organization, the conflicts that have the highest likelihood of occurring and that could have the potential for the most significant impact should be addressed first.
Whatever the remediation process—whether that’s a change to role structure, removal of user access, or use of compensating controls—it’s important to thoroughly document the resolution.
With respect to actual changes in the system, use existing processes, such as helpdesk tickets, to help ensure all changes are completed, accurate, and appropriately approved.
Setting Expectations
It’s unrealistic to expect perfect SOD compliance, especially during the first comprehensive review an organization performs. Ideally, all conflicts would be addressed through role redesign and shutting down unneeded access. However, it’s more likely that many conflicts will be institutionalized in the roles and responsibilities of the users. For these conflicts, changes to business processes and personnel capabilities will be necessary—and that can take time.
Lean Staffing Solutions
For smaller companies, there may not be enough qualified personnel to adequately segregate duties, and the cost of hiring additional personnel may not be justified by the benefits of strong SOD.
There are alternative approaches, provided an organization understands the risk created by known SOD conflicts. In these situations, it’s often possible to create compensating controls that are detective and preventive and that can mitigate risk through oversight and monitoring.
If SOD within the procurement process isn’t possible, for example, a robust bank reconciliation may mitigate the risk of inappropriate or fraudulent purchasing if performed by an independent and qualified person.
Frequency of Analysis
There’s no right or wrong answer to how often an SOD review should be performed. Many organizations perform reviews more frequently during periods of rapid change, such as growth, layoffs, or restructuring. Historical results will inform how often an assessment may be needed—the more issues that have been identified in the past, the more likely a higher frequency of analysis is required.
We’re Here to Help
For more information about how an SOD review could benefit your organization, contact your Moss Adams professional. You can also learn more by reading our SOD Report.