
Many life sciences companies invest in digital transformation by using technology to automate processes and data flow. Companies can run leaner, be more effective and efficient in their operations, and enhance customer and shareholder experience doing so.
But there are risks. How do you align the technology with your current business processes? Is your current system sufficient, or do you need changes? What are the cyber risks?
When done strategically, digital transformation can be especially beneficial for life sciences companies that have small head counts and focus most of their resources on internal product development.
We’ll touch on three aspects of a digital transformation strategy for life sciences companies:
What Is Digital Transformation?
Transforming business processes with technology can offer many benefits, but it’s important to assess existing systems first, understand potential challenges, and develop a strategy.
Digital Transformation Strategy Challenges
There are several significant challenges that your life sciences organization might face as you move through a digital transformation strategy.
Investment and Technology Application Costs
Digital transformation requires your organization to be able and willing to invest in technology to meet your strategic goals.
Changing Business and Employee Habits
There might be a limited understanding among employees of why the transformation is necessary. Poor planning, communication, and lack of stakeholder buy-in can lead to transformation misalignment.
Lack of Internal Resources
Most life sciences companies don’t have an abundance of labor force and operate with low headcounts and lean accounting departments.
Companies address low headcount by outsourcing a variety of internal activities to contract research organizations and contract manufacturing organizations; even technical accounting is often outsourced.
Lack of Digital Technology Infrastructure
There may not be a robust internal team to implement technology with a holistic view. Challenges can occur when there’s a heavy reliance on spreadsheets.
Slow Investment in Technology
Life sciences companies tend to focus on disbursements, payroll, and headcount associated with the science. The majority of transactions and activities are small volume, nonhomogeneous transactions.
This leaves little room to invest in technology, automation, and real time processing tools.
IT Systems and Infrastructure
Improving your internal business systems is a benefit of digital transformation. If any of your systems, such as enterprise resource planning (ERP), customer relationship management (CRM), or payroll, aren’t doing what they need to do, they might be worth assessing.
Learn more about improving your IT systems and infrastructure by watching our webcast.
Understand Common System Challenges
Before you begin an assessment of your current enterprise system, it can help to understand common system challenges.
Business Process Automation
Enterprise systems are supposed to reduce manual processes, allow for increased visibility across an organization, and help improve decision making.
If you already have an enterprise system but a particular business process isn’t automated, you may need a process-focused fit gap assessment.
Reporting Challenges
The ability to measure corporate performance is a hallmark of a truly powerful enterprise system. Qualities of an enterprise system with strong reporting capabilities include:
- Readily exportable to Excel, Word, or other third-party analysis systems
- Reliable reporting output requiring little analysis to reconcile the data
- Reasonable cost to maintain, not needing a dedicated data analyst or consultant
Internal Control and Compliance
Internal control and compliance are mandatory in many situations and may be both necessary and valuable in others. Failure to meet internal controls and regulatory compliance requirements within an enterprise system can lead to fraud, fines, or both.
Key compliance regulations include:
- Sarbanes-Oxley (SOX) Act compliance, including access, security, and change management
- 21 CFR park 11 compliance
- Current Good Manufacturing Practice and Food and Drug Administration (cGMP/FDA) validation requirements
- Sunshine Act/aggregate spend reporting
- HIPAA compliance
- Payment Card Industry (PCI) compliance
- General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA) compliance
Overall Poor Fit
In many cases, a combination of some or all of these creates the need to assess a system for visibility and scalability in support of all business processes. This is called a comprehensive fit gap assessment.
You’ll document and prioritize your organization’s functional requirements, and assess the system’s ability to meet them with a focus on:
- Technical platform of system
- System setup, configuration, and reporting
- Control and automation features
- Vendor roadmap for future upgrades and enhancements
- Integrated systems and other available solutions within the vendor ecosystem
Assess Existing Systems and Infrastructure
Below is a digital transformation roadmap detailing how to assess your existing systems and what to look for when in the process of replacing those systems.
Project Management and Change Enablement
Determine who’s going to guide the project, align digital transformation goals with strategic business goals, and communicate the plan to all parties and stakeholders.
Fact Finding
Learn about existing processes by:
- Interviewing process owners
- Identifying what’s working
- Identifying pain points
Then, review your findings to prioritize next steps.
Gap Analysis and Research
To perform a gap analysis, analyze system requirements, determine what functional and technical needs are not being met, and decide if an alternative solution is needed based on the desired end state.
Recommendation and Planning
Develop and document recommendations for your digital transformation, collaborate with the team to decide what needs to be prioritized first, and share the roadmap with stakeholders to gain buy-in.
Digital Transformation Solution Options
Once the system assessment has been completed, consider what to do. The initiatives that result from the assessment typically fall into three categories:
- Optimize or upgrade
- Integrate
- Replace
Optimize or Upgrade
This option typically occurs when a mid-range system hasn’t been configured correctly or features weren’t implemented that could help support business process automation and reporting needs.
Assess the return on investment (ROI) of a potential new system as well as the time required for desired optimizations or upgrades.
Integrate
Integration could be applicable when a cost-effective solution can be found within the partner ecosystem or an integrated third-party vendor.
Assess the total cost of the integration, including the license, the cost to implement, and ongoing costs, especially in terms of integration platform as a service.
Replace
If you have either outgrown the current system or it’s not hitting the mark, you can go through a new system selection process to replace the current system.
Internal Processes and Controls
In advanced technological environments, organizations can more reliably and consistently address risk if they can move to a more automated solution. IT-driven controls aren’t subject to human error, bias, or management override.
Learn more about strengthening internal processes by watching our webcast.
Companies can use the following controls to assist in their accounting.
Manual Controls
Though technology can be used to supplement manual controls, there will always be instances where management will need to make a subjective conclusion on a complex topic. This must be done via some type of human intervention.
Consider manually monitoring the following:
- Management review controls (MRCs)
- Estimates or accruals and other dissemination of critical information
- R&D spend expectations and percentage complete
- Vendor banking details
Spreadsheets and End-User Controls (EUCs)
In spreadsheet-heavy environments, organizations can establish entity-wide programs to help manage EUCs.
The following are strategies to implement that support security if your organization uses spreadsheets:
- Maintain accurate inventory of all discovered, registered, and managed files
- Implement version, access, change, and data integrity controls
- Establish procedures that monitor changes to inputs and logic
- Restrict access to spreadsheets so that only supervisors have access to unlock cells
- Leverage Excel add-ons and embedded applications, such as Smartsheet, Tableau, or Domo
IT Application Controls (ITACs)
ITACs include safeguards in relation to specific applications. ITACs prevent, detect, and correct transaction errors and fraud in application programs. They are concerned with the accuracy, completeness, validity, and authorization of the data captured, stored, transmitted to other systems, and reported.
Several types of application controls exist with the objective to ensure that input and output data are accurate and complete, processed in an acceptable time, and a record is maintained to track the process of data from input to storage and to the eventual output.
Examples of application controls are:
- Ensuring goods and services are only procured with an approved purchase order
- Monitoring segregation of duties based on defined job responsibilities
- Identifying that received goods and services are accurate upon receipt
- Ensuring fixed-asset depreciation is recorded accurately in the appropriate accounting period
- Determining whether there’s a three-way match among the purchase order, receiver, and vendor invoice
IT General Controls (ITGCs)
ITGCs refer to the overarching controls that relate to security, change management, and the use or design of computer programs. They ensure an organization’s control environment is stable and well-managed, including the IT infrastructure and software acquisition, development, and maintenance.
Several types of ITGCs exist with the objective to ensure that system and organization controls (SOC) reports for cloud-based systems are assessed for unmitigated risks, security and access to systems and key reports are limited via least privilege, and there is control over batch processing.
Because life sciences companies rely heavily on third parties, managing third-party risk is critical. Are you outsourcing IT or R&D? If so, work with vendors who have current SOC reports.
Organizations can gain significant effectiveness and efficiency in maintaining internal controls over financial reporting by following the steps needed to maintain this strong IT general control environment.
Automated Workflows
To further strengthen your internal processes and controls, you can utilize automated process workflows.
Examples of automated process workflows include:
- Journal entry approval
- New vendor approval
- Vendor bill approval
- Vendor payment
- Purchase order and purchase request
Defining Scripts
Gain some efficiency and effectiveness in your operations using scripts. A script is a program or sequence of instructions that takes a series of commands and turns it into a single command. With one click, the script can run several sequential tasks.
A common example is using scripts for payroll processes.
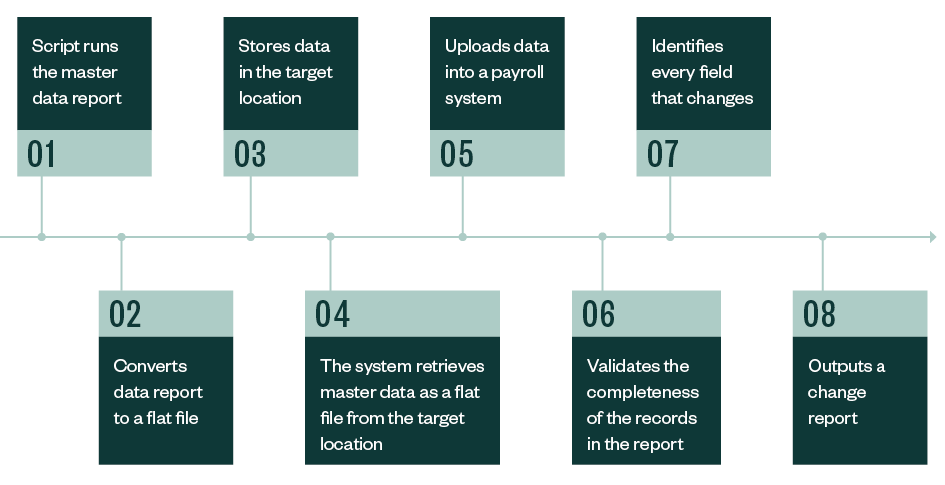
There are many individual activities during this process, but with a script, the system is programmed to run the activities consistently and without error.
The script will let the user know if an error occurs. Scripts can be a very potent and effective tool for increasing the effectiveness and efficiency of your operations.
Cybersecurity
Cybersecurity should be a significant consideration as your organization develops a digital transformation strategy.
Data that’s held on your network or in the cloud, such as intellectual property (IP), financial data, employee information, clinical trial information, and research results are enticing to bad actors and are at risk. Through a variety of strategies, such as phishing, ransomware, and social engineering, bad actors can try to find and exploit vulnerabilities.
If you can apply practical security through these basic hygiene measures, then you can remove some of those opportunities and decrease the risk of an attacker infiltrating your network.
Learn more about the strategies to improve cybersecurity by watching our webcast.
Below are eight areas to focus on to lower the risk of a cyberattack and reduce data loss.
Security Awareness Training
There are reasonable, robust, and readily available ways to train and test employees with realistic, orchestrated phishing and social engineering campaigns—two common methods bad actors use to gain access to a network.
Train employees to inspect URLs before clicking on any links or images in their emails and conduct regular tests to help employees become familiar with phishing emails and malicious links.
Identity and Access Management
There are several principles that are very important from a security perspective around identity and access management.
- Least privilege. Give administrative access to only those who need it to perform their job.
- Segregation of duties. One person shouldn’t complete an entire process from start to finish by without oversight.
- Reviews. Review user accounts for unknown users or suspicious user activity.
- Privileged access management. Establish controls so that administrative accounts are only used when necessary.
- Robust authentication methods. Create complex passwords or utilize multifactor authentication to boost security and prevent attacks.
Device and Software Inventory
Maintaining accurate inventory of all software and hardware is a foundational and critical part of a cybersecurity program. It’s important that inventory records of approved hardware and software are accurate so that accepted controls can be implemented to protect hardware and software from threats.
Maintaining inventories can be done manually with spreadsheets, passively with a device or software that listens to network traffic, or actively, with software that’s constantly scanning the network for active devices.
Implementing some type of inventory process enables faster remediation. If something happens, it’s easier to remedy the issue if there’s an accurate inventory list to determine which devices are the problem.
Accurate inventories also simplify the decommission process. Attackers look for outdated, vulnerable servers and software. An inventory can make it easier to assess devices and determine what needs to be updated or decommissioned.
Vulnerability Management
A vulnerability management program can be multipronged. Two important aspects are patching and antivirus.
- Patching. When a software bug is found, developers, testing teams, and security researchers will issue a patch, which is a piece of software that remedies that bug and fixes it with new code
- Antivirus. When vulnerabilities within software programs are found, attackers could write a program, or virus, to leverage those vulnerabilities
Auditing and Logging
Logging software activity can happen at the application level—each action a user takes—and the application level—the number of connections, memory spikes, or high CPU usage indicating malicious activity.
Benefits of creating an auditing and logging process include finding inefficiencies, identifying attackers, and increased visibility.
Data Encryption
For life sciences companies, one of the biggest business assets may be your data. Determine what data is the most sensitive and what data is the most highly valued.
The value and sensitivity of your data will help determine what protections you put in place, such as how you access it, who uses it, and the availability.
Encryption
For data in storage or in transit, there should be a level of encryption for these environments. Encrypting data stores and data transmissions could prevent you from having to pay regulatory fines should you be attacked.
To protect data, look at your firewall settings, make sure you're using the most up to date transport layer security, and implement a file integrity monitoring system.
Data Back-Ups
Data that’s backed up should have the same level of security, or more, as data in the production environment. Production data and data backups should both be encrypted with strong encryption keys.
Determine how often this data is being overwritten, when it will be archived, if it has continuous data protection, and who’s responsible for the data.
Incident Response, Disaster Recovery, and Business Continuity Planning
How resilient is your organization when it comes to a data breach? Attacks are just a question of when.
- Prioritize. Make cybersecurity a priority in your company
- Train. Staff should be trained, and training should encompass members from many different departments
- Perform a business impact analysis. Identify critical data, critical business functions, services, and IT equipment that could be impacted in the event of a cyberattack
- Test. Incident response plans should be tested on a regular basis and can help reduce the time it takes to recover from an attack
- Respond. Timely response after an internal attack, or when a supplier or vendor is attacked, is critical
Cyber Supply Chain Risk Management
Supply chain risk management is being aware of any additional risk that’s being introduced into your organization through an outside supplier, vendor, or software. If providers are at a high risk, you may not want to do business with them.
Vet a new provider to help identify any potential problems before you sign a contract. With new or existing suppliers or vendors, you can monitor what they’re doing with your data, including when they’re accessing data, why they need access, and who’s accessing it. You can also log the activity to assess what happened in the event of an attack.
After a provider has been offboarded you can continue to keep security in mind by removing access to your network and email and request that third-party service providers turn over all data in their environment or provide proof data has been rendered unreadable.
We’re Here to Help
For guidance on creating and implementing a digital transformation strategy, contact your Moss Adams professional.
You can also visit our Life Sciences Practice page for additional resources.