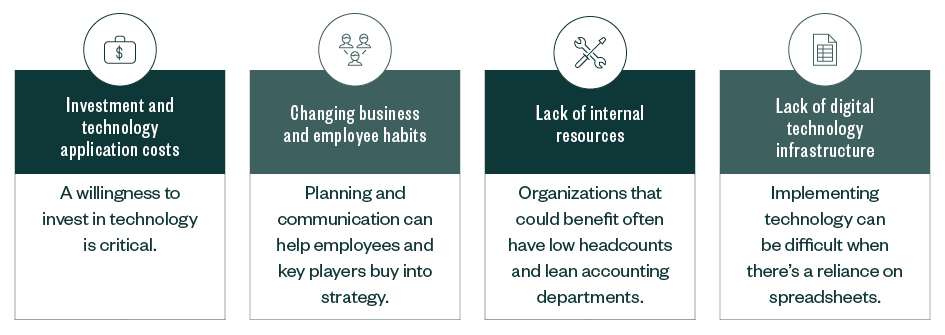
Digital Transformation Strategy Challenges
Cybersecurity
Cybersecurity should be a significant consideration as your organization develops a digital transformation strategy—including understanding what the risks are and how to mitigate them.
What Are Cybersecurity Risks?
Data held in your network or in the cloud, such as intellectual property (IP), financial data, employee information, or client or customer data, can be targeted by bad actors. Through a variety of strategies, such as phishing, ransomware, and social engineering, bad actors can try to find and exploit vulnerabilities.
How to Mitigate Cybersecurity Risks
If you can apply practical security through these basic hygiene measures, then you can reduce exploitation opportunities and reduce the risk of an attacker infiltrating your network.
Below are eight areas to focus on to lower the risk of a cyberattack and reduce data loss while developing and implementing a digital transformation strategy.
Security Awareness Training
There are reasonable, robust, and readily available ways to train and test users with realistic, orchestrated, phishing and social engineering campaigns.
Train users to inspect URLs before clicking on any links or images in their emails and conduct regular tests to help employees become familiar with phishing emails and malicious links. Provide users with guidance for reporting suspicious emails to the cybersecurity department, such as a phish alert.
Identity and Access Management
There are several important security principles around identity and access management.
- Limit privilege. Grant user access to the company network based on job roles, also known as role-based access.
- Segregation of duties. Establish checks and balances; one user shouldn’t complete an entire process from start to finish without oversight.
- Reviews. Regularly review user accounts to determine if access is still appropriate for certain users.
- Privileged access management. Establish controls so that administrative accounts are only created and used when necessary.
- Robust authentication methods. Create complex passwords or utilize multifactor authentication to enhance security and prevent attacks.
Device and Software Inventory
Maintaining accurate inventory of all software and hardware is a foundational and critical part of a cybersecurity program. It’s important that inventory records of approved hardware and software are accurate so accepted controls can be implemented to protect hardware and software from threats.
Maintaining inventories can be done manually with spreadsheets, passively with a device or software that listens to network traffic, or actively, with software that’s continuously scanning the network for active devices.
A solid inventory program allows for more effective remediation of hardware and software vulnerabilities. When updates or patches are needed, it’s more effective to identify assets that need to be updated if the inventory records are up to date; otherwise, hardware and software can become outdated over time, which increases risk to the business.
Accurate inventories also simplify the decommission process. Attackers look for outdated, vulnerable servers and software. An inventory can make it easier to assess devices and determine what needs to be decommissioned and removed from the network.
Vulnerability Management
A vulnerability management program can be multipronged. Two important aspects are patching and antivirus:
- Patching. When a software vulnerability is identified, developers, testing teams, and security analysts will issue a patch, which is a piece of software that remedies that vulnerability and corrects it with new code
- Antivirus. When vulnerabilities within software programs are found, attackers could write a program, or virus, to leverage those vulnerabilities
Auditing and Logging
Logging software activity can happen at two levels:
- Application level. The actions each user takes
- Operating system level. The number of connections, memory spikes, or high CPU usage
Benefits of creating an auditing and logging process include increased visibility, finding inefficiencies, and identifying attackers and malicious activity.
Data Encryption
Data is many companies' biggest business asset, so determining what data is most sensitive and most highly valued is paramount.
The value and sensitivity of your data and regulatory requirements will help determine what protections you put in place, such as how you access it, who uses it, and the availability.
Encryption
For data in storage or in transit, there should be a level of encryption for these environments. Encrypting data stores and data transmissions could prevent you from having to pay regulatory fines if data is inappropriately access or disclosed.
To protect data, look at your firewall settings, make sure you're using the most up to date transport layer security, and implement a file integrity monitoring system. A comprehensive data loss prevention program can help identify and address the risk of how data can be inappropriately accessed or disclosed, and how the to reduce the occurrence of these events.
Data Back-Ups
Data that’s backed up should have the same level of security, or more, as data in the production environment. Production data and data backups should both be encrypted with strong encryption keys.
Determine how often data is being overwritten, when it will be archived, if it has continuous data protection, and who’s responsible for the data. Identify and document all regulatory requirements for maintaining data over time before destroying data archives.
Incident Response, Disaster Recovery, and Business Continuity Planning
How resilient is your organization when it comes to a data breach? Attacks are just a question of when.
- Prioritize. Make cybersecurity a priority in your company
- Train. Staff should be trained, and training should encompass members from many different departments
- Perform a business impact analysis. Identify critical data, critical business functions, services, and IT equipment that could be impacted in the event of a cyberattack
- Test. Incident response plans should be tested on a regular basis and can help reduce the time it takes to recover from an attack
- Respond. Timely response after an internal attack, or when a supplier or vendor is attacked, is critical
Cyber Supply Chain Risk Management
Supply chain risk management is being aware of any additional risk introduced into your organization through an outside supplier, vendor, or software. If providers are at a high risk, you may not want to do business with them.
Vet a new provider to help identify any potential problems before you sign a contract. With new or existing suppliers or vendors, you can monitor what they’re doing with your data, including when they’re accessing data, why they need access, and who’s accessing it. You can also log the activity to assess what happened in the event of an attack.
After a provider has been offboarded, you can continue to keep security in mind by removing access to your network and email and request that third-party service providers turn over all data in their environment or provide proof data has been rendered unreadable.
We’re Here to Help
For guidance on creating and implementing a digital transformation strategy, contact your Moss Adams professional.
Visit our Cybersecurity services for more information.

